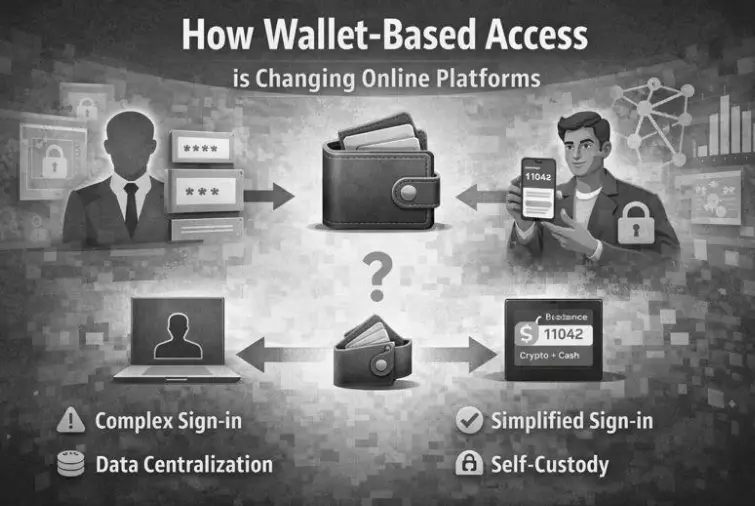
You’ve probably noticed something if you’ve spent any time in crypto spaces lately. That familiar “create account” flow, email, password, phone verification, maybe a document upload — keeps getting replaced by something simpler. Connect wallet. Done.
It feels almost too easy. And that simplicity is exactly the point.
So What’s Actually Happening Here?
Traditional platforms treat your identity as the key to the door. You prove who you are, they grant access, and your personal information lives on their servers indefinitely. It’s the model we’ve used since the early internet days, and honestly, most people never questioned it.
Blockchain introduced a different idea entirely.
What if access didn’t require identity at all? What if proving you control something mattered more than proving you are someone?
That’s wallet-based access in a nutshell. Your crypto wallet becomes your credential. No name required. No documents scanned. The system cares about one thing: can you cryptographically prove you control this wallet? Yes? You’re in.
Why Developers Started Building This Way
Building platforms around identity verification isn’t cheap. There’s compliance overhead, document storage, security infrastructure, support teams handling “I forgot my password” requests. For platforms handling millions of users, these costs stack up fast.
Wallet-based systems sidestep most of that.
The user handles their own security. The platform doesn’t store sensitive documents that could get breached. Onboarding takes seconds instead of days. For developers building in the crypto ecosystem, it’s a practical choice as much as a philosophical one.
But there’s something deeper going on too. When platforms collect your data, they become targets. Every exchange hack, every leaked database — those breaches happen because centralized honeypots of personal information attract attackers. Remove the honeypot, reduce the risk.
What Your Wallet Actually Does
Think of a traditional account like a hotel key card. The hotel programs it, the hotel can deactivate it, and the hotel knows exactly which room you’re in. Convenient, but you’re trusting the hotel completely.
A wallet works more like owning your own key to your own property. Nobody programmed it for you. Nobody can revoke it remotely. And unless you hand someone the key, nobody else gets in.
When you connect a wallet to a platform, you’re not handing over credentials. You’re proving ownership through cryptographic signatures — mathematical proof that you control what you claim to control. The Ethereum Foundation’s documentation on wallets explains this well: wallet providers don’t actually hold your funds. They just give you a window to see and manage assets that exist on the blockchain itself.
This distinction matters. You’re not trusting the platform with your assets. You’re using the platform while maintaining custody yourself.
Where You’ll Actually Encounter This?
Wallet connections have become standard across most crypto. DeFi protocols, NFT marketplaces, decentralized exchanges — nearly everything in that ecosystem works this way now.
But it’s spreading beyond pure crypto applications.
Gaming platforms are adopting wallet logins for in-game asset ownership. Some content platforms let creators receive payments directly to connected wallets. The model extends beyond finance too. A growing number of No KYC casino platforms now operate purely through wallet connections — no account creation, no ID verification, just connect and play.
The common thread? These services prioritize speed and user control over collecting identity data.
The Part Nobody Wants to Talk About
Here’s where things get uncomfortable. All that convenience comes with a serious tradeoff.
When you manage your own wallet, you are the security department. There’s no “forgot password” link. No support ticket to file. No fraud team reviewing suspicious activity on your behalf.
Lose your seed phrase? Those funds are gone. Fall for a phishing site and sign a malicious transaction? Nobody’s reversing it. Send to the wrong address? Hope whoever controls it feels generous.
These aren’t hypothetical risks. People lose meaningful amounts of money this way regularly. The crypto space has a saying: “not your keys, not your coins.” The flip side is equally true — your keys, your problem.
Who This Model Actually Works For?
Let’s be honest about fit.
Wallet-based access works beautifully for people who already understand crypto fundamentals. They know what a seed phrase is and why it matters. They understand transaction signing. They’ve probably been burned at least once and learned from it.
For everyone else? The learning curve is real.
This isn’t gatekeeping — it’s acknowledging that self-custody requires skills most internet users have never needed before. Traditional platforms handle security so users don’t have to. Wallet-based systems flip that responsibility entirely.
Someone who’s uncomfortable with the idea of being solely responsible for their access probably shouldn’t be using these platforms yet. That’s not a criticism of them. It’s a recognition that different models suit different users.
What Makes This Relevant in the UAE
The Emirates have embraced digital transformation faster than almost anywhere else. Digital banking features from institutions like FAB show how comfortable residents are with managing finances through apps and online portals. The infrastructure here supports cutting-edge fintech adoption.
But there’s also a strong culture of personal accountability. UAE residents don’t expect someone else to fix their problems. They understand that advanced tools require advanced responsibility.
That mindset aligns naturally with wallet-based models. Privacy-conscious users who value control over their data find these systems appealing. They’re not looking for hand-holding — they’re looking for tools that respect their autonomy.
The question isn’t whether wallet-based access is “better.” It’s whether it matches how you want to interact with digital platforms.
Verification Didn’t Disappear – It Changed Shape
One misconception worth clearing up: wallet-based platforms aren’t verification-free zones. They just verify different things.
Instead of checking your passport, they check whether your transaction is valid. Instead of confirming your address, they confirm your wallet holds what it claims to hold. Instead of storing your documents, they record actions on an immutable ledger.
Everything gets verified. The verification just happens at the action level rather than the identity level. Transparency exists — often more transparency than traditional platforms offer — but it’s structural rather than personal.
Making the Choice
Nobody’s forcing a binary decision here. Most people who engage with crypto maintain both options: verified accounts on regulated exchanges for fiat on-ramps and larger holdings, wallet-based access for DeFi interactions and privacy-sensitive activities.
The two models serve different purposes. Traditional verification makes sense when you want institutional protections and recourse options. Wallet-based access makes sense when you prioritize speed, privacy, and direct control.
Knowing which situation calls for which approach is part of becoming crypto-literate.
Where This Is Heading?
Platform design increasingly reflects user expectations. People want options. They want to choose their own tradeoff between convenience and control, between privacy and protection.
The smartest platforms offer tiered access — basic functionality with minimal friction, additional features unlocked through progressive verification. Users decide how much information they’re willing to share based on what they’re trying to accomplish.
Wallet-based access isn’t replacing traditional verification everywhere. But it’s established itself as a legitimate alternative — one that’s here to stay and expanding into new categories.
For users who understand the model and accept its tradeoffs, it represents something genuinely different: platforms that work for you without needing to know you.